 |  |

A firewall system is an essential component of network security. The term "firewall" implies protection from danger, and just as the firewall in your car protects the passengers' compartment from the car's engine, a firewall computer system protects your network from the outside world. A firewall computer system provides strict access control between your systems and the outside world.
The concept of a firewall is quite simple. A firewall is a choke point through which all traffic between a secured network and an unsecured network must pass. In practice, it is usually a choke point between an enterprise network and the Internet. Creating a single point through which all traffic must pass allows the traffic to be more easily monitored and controlled and allows security expertise to be concentrated on that single point.
Firewalls are implemented in many ways. In fact, there are so many different types of firewalls, the term is almost meaningless. When someone tells you they have a firewall, you really can't know exactly what they mean. Covering all of the different types of firewall architectures requires an entire book -- see Building Internet Firewalls (O'Reilly & Associates). Here we cover the screened subnet architecture (probably the most popular firewall architecture) and the multi-homed host architecture, which is essentially a firewall-in-a-box.
The most common firewall architecture contains at least four hardware components: an exterior router, a secure server (called a bastion host), an exposed network (called a perimeter network), and an interior router. Each hardware component provides part of the complete security scheme. Figure 12-4 illustrates this architecture.
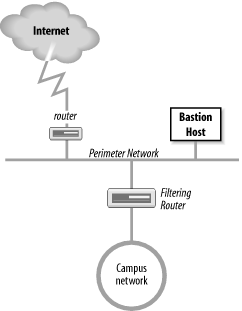
The exterior router is the only connection between the enterprise network and the outside world. This router is configured to do a minimal level of access control. It checks to make sure that no packet coming from the external world has a source address that matches the internal network. If our network number is 172.16, the exterior router discards any packets it receives on its exterior interface that contain the source address 172.16. That source address should be received by the router only on its interior interface. Security people call this type of access control packet filtering .
The interior router does the bulk of the access control work. It filters packets not only on address but also on protocol and port numbers to control the services that are accessible to and from the interior network. It's up to you which services this router blocks. If you plan to use a firewall, the services that will be allowed and those that will be denied should be defined in your security policy document. Almost every service can be a threat. These threats must be evaluated in light of your security needs. Services that are intended only for internal users (NIS, NFS, X-Windows, etc.) are almost always blocked. Services that allow writing to internal systems (Telnet, FTP, SMTP, etc.) are usually blocked. Services that provide information about internal systems (DNS, fingerd, etc.) are usually blocked. This doesn't leave much running! That is where the bastion host and perimeter network come in.
The bastion host is a secure server. It provides an interconnection point between the enterprise network and the outside world for the restricted services. Some of the services that are restricted by the interior gateway may be essential for a useful network. Those essential services are provided through the bastion host in a secure manner. The bastion host provides some services directly, such as DNS, SMTP mail services, and anonymous FTP. Other services are provided as proxy services. When the bastion host acts as a proxy server, internal clients connect to the outside through the bastion host, and external systems respond back to the internal clients through the host. The bastion host can therefore control the traffic flowing into and out of the site to any extent desired.
There can be more than one secure server, and there often is. The perimeter network connects the servers together and connects the exterior router to the interior router. The systems on the perimeter network are much more exposed to security threats than are the systems on the interior network. This is as it must be. After all, the secure servers are needed to provide service to the outside world as well as to the internal network. Isolating the systems that must be exposed on a separate network lessens the chance that a compromise of one of those systems will lead directly to the compromise of an internal system.
The multi-homed host architecture attempts to duplicate all of these firewall functions in a single box. It works by replacing an IP router with a multi-homed host that does not forward packets at the IP layer.[140] The multi-homed host effectively severs the connection between the interior and exterior networks. To provide the interior network with some level of network connectivity, it performs similar functions to the bastion hosts.
[140]The role of IP routers, also called gateways, in gluing the Internet together is covered extensively in earlier chapters.
Figure 12-5 shows a comparison between an IP router and a multi-homed host firewall. A router handles packets up through the IP layer. The router forwards each packet based on the packet's destination address, and the route to that destination indicated in the routing table. A host, on the other hand, does not simply forward packets. A multi-homed host can process packets through the Application Layer, which provides it with complete control over how packets are handled.[141]
[141]See Chapter 5, "Basic Configuration " for information on how to prevent a multi-homed host from forwarding packets.
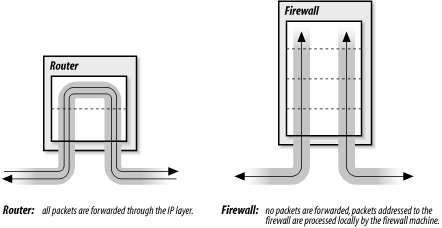
This definition of a firewall -- as a device completely distinct from an IP router -- is not universally accepted. Some people refer to routers with special security features as firewalls, but this is really just a matter of semantics. In this book, routers with special security features are called "secure routers" or "secure gateways." Firewalls, while they may include routers, do more than just filter packets.
Ideally, an intruder cannot mount a direct attack on any of the systems behind a firewall. Packets destined for hosts behind the firewall are simply delivered to the firewall. The intruder must instead mount an attack directly against the firewall machine. Because the firewall machine can be the target of break-in attacks, it employs very strict security guidelines. But because there is only one firewall versus many machines on the local network, it is easier to enforce strict security on the firewall.
The disadvantage of a firewall system is obvious. In the same manner that it restricts access from the outside world into the local network, it restricts access from the local network to the outside world. To minimize the inconvenience caused by the firewall, the system must do many more things than a router does. Some firewalls provide:
DNS name service for the outside world
Email forwarding
Proxy services
Only the minimal services truly needed to communicate with external systems should be provided on a firewall system. Other common network services (NIS, NFS, X Windows, finger, etc.) should generally not be provided. Services are limited to decrease the number of holes through which an intruder can gain access. On firewall systems, security is more important than service.
The biggest problems for the firewall machine are ftp service and remote terminal service. To maintain a high level of security, user accounts are discouraged on the firewall machine; however, user data must pass through the firewall system for ftp and remote terminal services. This problem can be handled by creating special user accounts for ftp and telnet that are shared by all internal users. But group accounts are generally viewed as security problems. A better solution is to allow ssh services through the firewall. This encourages the use of ssh, which in turn provides strong authentication and encrypted data exchanges.
Because a firewall must be constructed with great care to be effective, and because there are many configuration variables for setting up a firewall machine, vendors offer special firewall software. Some vendors sell special-purpose machines designed specifically for use as firewall systems. There are several low-cost Linux firewall packages. Before setting up your own firewall, investigate the options available from software vendors and your hardware vendor.
The details of setting up a firewall system are beyond the scope of this book. Before you proceed, I recommend you read Building Internet Firewalls and Firewalls and Internet Security. Unless you have skilled Unix system administrators with adequate free time, a do-it-yourself firewall installation is a mistake. Hire a company that specializes in firewall design and installation. If your information is valuable enough to protect with a firewall, it should be valuable enough to protect with a professionally installed firewall.
Of course, not every site can afford a professionally installed firewall -- you might be protecting a small office or even a home network. If you don't have money or time, you can buy a low-cost firewall router, sometimes referred to as a firewall appliance. These boxes are specifically designed for the small office and home office. They provide basic packet filtering, proxy services, and network address translation service, and they often cost only a few hundred dollars. In most cases, you simply buy the box and plug it in. At the very least, your network deserves this level of protection. If you have the time and the skill to build a firewall, you can use a firewall package or the firewall tools built into your operating systems. A firewall package increases initial cost, but it is easy to work with. The packet filtering tools built into the operating system cost nothing but are the most difficult to configure. The iptables tool provided with Linux is a good example of the type of firewall tools provided with some Unix operating systems.
In its simplest incarnation, a firewall is a filtering router that screens out unwanted traffic. Use the routing capabilities of a multi-homed Linux host combined with the filtering features of iptables to create a filtering router.
The Linux kernel categorizes firewall traffic into three groups and applies different filter rules to each category of traffic. These are:
Incoming traffic bound for a process on the local system is tested against the INPUT filter rules before it is accepted.
Outbound traffic that initiated on the local system is tested against the OUTPUT filter rules before it is sent.
Traffic from one external system bound for another external system is tested against the FORWARDING filter rules.
The INPUT and OUTPUT rules are used when the system acts as a host. The FORWARD rules are used when the system acts as a router. In addition to the three standard categories, iptables accepts user-defined categories.
The Linux kernel maintains a list of rules for each of these categories. The lists of rules are maintained by the iptables command.[142] Use the options shown in Table 12-2 with the iptables command to create or delete user-defined chains, to add rules to a chain, to delete rules from a chain, and to change the order of the rules in the chain.
[142]iptables came into use with Linux kernel 2.4. Early kernels used the ipfwadm and the ipchains commands. See Linux Firewalls by Robert Ziegler (New Riders, 2000) for information on these older commands.
|
Option |
Function |
|---|---|
|
-A |
Appends rules to the end of a ruleset. |
|
-D |
Deletes rules from a ruleset. |
|
-E |
Renames a ruleset. |
|
-F |
Removes all of the rules from a ruleset. |
|
-I |
Inserts a rule into a specific location in a ruleset. |
|
-L |
Lists all rules in a ruleset. |
|
-N |
Creates a user-defined ruleset with the specified name. |
|
-P |
Sets the default policy for a chain. |
|
-R |
Replaces a rule in a chain. |
|
-X |
Deletes the specified user-defined ruleset. |
|
-Z |
Resets all packet and byte counters to zero. |
Firewall rules are composed of a filter against which the packets are matched and the action taken when a packet matches the filter. The action can either be a standard policy or a jump to a user-defined ruleset for additional processing. The -j target command-line option identifies the user-defined ruleset or the standard policy to handle the packet. target is either the name of a ruleset or a keyword that identifies a standard policy. The keywords for the standard policies are:
Let the packet pass through the firewall.
Discard the packet.
Pass the packet up to user space for processing.
In a user-defined ruleset, this means to return to the ruleset that called this ruleset. In one of the three kernel rulesets, this means to exit the chain and use the default policy for the chain.
The iptables command constructs filters that match on the protocol used, the source or destination address, or the network interface used for the packet, using a variety of command-line parameters. The basic iptables parameters for building filters are:
Defines the protocol to which the rule applies. protocol can be any numeric value from the /etc/protocols file or one of the keywords: tcp, udp, or icmp.
Defines source address of the packets to which the rule applies. address can be a hostname, network name, or IP address.
Defines the source port of the packets to which the rule applies. port can be a name or number from the /etc/services file. A range of ports can be specified using the format port:port. If no specific port value is specified, all ports are assumed.
Defines the destination address of the packets to which the rule applies. address can be a hostname, network name, or IP address.
Defines the destination port to which the rule applies. This filters all traffic bound for a specific port. The port is defined using the same rules as those used to define these values for the packet source.
Defines the ICMP type to which the rule applies. type can be any valid ICMP message type number or name.
Defines the name of the input network interface to which the rule applies. Only packets received on this interface are affected by the rule. Specify a partial interface name by ending it with a + (e.g., eth+ matches all Ethernet interfaces that begin with eth).
Defines the name of the output network interface to which the rule applies. Only packets sent out this interface are affected by the rule. Specify a partial interface name by ending it with a + (e.g., eth+ matches all Ethernet interfaces that begin with eth).
Indicates that the rule refers only to second and subsequent fragments of fragmented packets.
Putting this all together creates a firewall that can protect your network. Assume we have a Linux router attached to a perimeter network with the address 172.16.12.254 on interface eth0 and to an external network with the address 192.168.6.5 on interface eth1. Further assume that the perimeter network contains only a sendmail server and an Apache server. Here is an example of some iptables commands we might use on the Linux system to protect the perimeter network:
iptable -F INPUT iptables -F FORWARD iptables -A INPUT -i eth1 -j DROP iptables -A FORWARD -i eth1 -s 172.16.0.0/16 -j DROP iptables -A FORWARD -o eth1 -d 172.16.0.0/16 -j DROP iptables -A FORWARD -d 172.16.12.1 25 -j ACCEPT iptables -A FORWARD -d 172.16.12.6 80 -j ACCEPT iptables -A FORWARD -j DROP
The first two commands use the -F option to clear the rulesets we plan to work with. The third line drops any packets from the external network that are bound for a process running locally on the Linux router. We do not allow any access to router processes from the external world.
The next two commands drop packets that are being routed to the external world using an internal address. If packets are received on the external interface with a source address from the internal network, they are dropped. Likewise, if packets are being sent out the external interface with a destination address from the internal network, they are dropped. These rules say that if packets on the external network interface (eth1) misuse addresses from the internal network (172.16), somebody is trying to spoof us and the packets should be discarded.
The next two rules are basically identical. They accept packets if the destination and port are the correct destination and port for a specific server. For example, port 25 is the SMTP port and 172.16.12.1 is the mail server, and port 80 is the HTTP port and 172.16.12.6 is the web server. We accept these inbound connections because they are destined for the correct systems. The last rule rejects all other traffic.
These examples illustrate the power of Linux's built-in filtering features and provide enough information to get you started. Clearly much more can and should be done to build a real firewall. If you want to know more about iptables, see Building Internet Firewalls and Linux Security, both mentioned in the reading list below, for many more detailed examples.

Copyright © 2002 O'Reilly & Associates. All rights reserved.